CloudFoxy Acclaim
CloudFoxy is built on an acclaimed platform, which has been presented at best security conferences and events in the world - from DEFCON, to BlackHat and ACM Conference on Communication Security (one of the top events in the world of encryption research). The platform was used to demonstrate an encryption system resistant to attacks including supply-chain subversion.
CloudFoxy builds on the excellence of the hardware platform and couples it with simple integration and practical use-cases you can use out of the box.
… a high level of compatibility between manufacturers and this allows to efficiently distribute [encryption] computations across multiple devices.
An independent blinded review - expert on encryption technologies
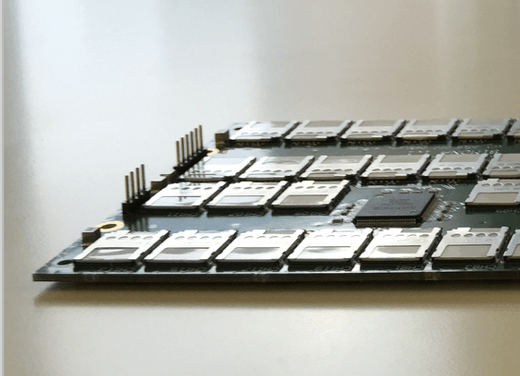
Visit http://opencryptojc.org for developer resources
OPENCRYPTO: Unchaining The Javacard Ecosystem
BlackHat USA, 2017 (Las Vegas, Nevada)
-
JavaCards are an affordable and convenient way of separating security critical code and secrets
-
You can use JavaCard code in local hardware, cloud JavaCards, or in
simulators (local or listening on an TCP/IP port)
-
JCMath Lib fills the gap in modern crypto algorithms - Elliptic Curve Encryption (ECC)
-
Get started right-away
-
Examples & Documentation
-
-
Profiler & Complete Toolchain
More presentation videos and information at https://enigmabridge.com/mpc.html
Trojan-tolerant Hardware & Supply Chain Security in Practice
DEFCON 25, Las Vegas, USA
New crypto hardware architecture
-
For the first time, tolerates faulty & malicious hw
-
Decent Performance
-
Scales nicely; just keep adding ICs
-
Suitable for commercial-off-the-shelf components
CloudFoxy is a brand of Smart Arcs Ltd, a company registered in England and Wales - reg. no.: 07359131. The registered address of Smart Arcs Ltd is ideaSpace, 3 Charles Babbage Rd, CB3 0GT United Kingdom.
Click here to read our terms and conditions and privacy statement of this website.